Network Security Essay
-
Tamara Team
- December 25, 2022

System Proposal, Susceptibility to Network Hackers
Network Security Essay Introduction
In the last decades, the world has become quite digital and dependent on cutting-edge electronic and networking devices such as computers and smartphones. With this digitalization, many private health and government institutions tend to adapt their data collection to digital networks (“Industrial Network Security,” 2016). Although this approach creates a fast and practical data handling environment, the scope of stealing data (or hacking in today’s world) has become much more remote and accessible. In other words, a competent and advanced hacker can now steal the data of thousands of patient information from a hospital’s database, when it is not properly protected by the networking agents. This assignment presents a system proposal regarding network and data security in such organizations, and it highlights the fact that these measures should be taken to combat effectively against hacking and susceptibility to network hackers.
Network Security Issue
The ongoing trend of network and data hacking have become an issue across the world. Accordingly, many health institutions and nursing informatics have been negatively affected by the drawbacks of the digitalizing world. To overcome such an issue, several recommendations will be made. Most importantly, the goal for this project is to ensure patient data safety in the digital databases.
Background of the Problem
In general, computer and network hacking refer to have direct access to other networks and computers without the owner’s permission. In this sense, if a hacker can sneak into a network or database of an organization, the data and even credit card information of patients or customers can easily be stolen, and this issue will create drastic problems for organizations and businesses (The Effects of Computer Hacking on an Organization, 2019). Furthermore, hackers can erase the data and backup, which is much more fatal for the organization.
“Networking provides access to countless opportunities for nurses and patients and allows them to communicate, interact, and collaborate with each other in order to enhance nursing care practice and improve health” (“Healthcare Under Attack,” 2018; Khanum et al., 2016, para. 2). Therefore, the role of networking and data tools are not negligible in nursing, and they create useful practices for both sides. In this direction, many research has already highlighted the increasing trend of hacking in the digital world. When considered the fact that nursing and health institutions are now quite associated with network and data systems, identifying a digital problem of hacking data and networks is now quite critical for authorities.
Proposed Solutions for Network Security
Email security
Emails are the first reason for malware into a network. “Given all the data that have pointed to this as the root cause of many breach events, it should be the first place where organizations take the time to be informed patients or consumers in this regard and understand the threat of email” scum and spamming of hackers (Hacking Prevention, 2020, para. 7).
End-point Detection and Response
In general, most of the emails are designed for a user to click on. Malicious web content is the second most reason for malware and hacking. Therefore, Nursing Informacisits should implement scheduled end-point link controls of email interaction within an organization. In this direction, malware, shutdown viruses, and other unwanted programs can be identified by the tech team before creating potential damage to the network and data.
Multi-step / Multi-factor Authentication
After all, one of the most common causes of hacking and breaching to a network is the hacking of login credentials of admins or other users with limited admin rights to databases or network. In parallel with this claim, many internet-based companies and organizations have already turned to such system to ensure both admin and user data and network safety (Hacking Prevention, 2020). Accordingly, health institutions should implement multi-factor authentication to their network and data system logins in order to prevent possible breaching threats and loss of patient data.
Cloud-based database services also provide mobility. As the business grows, mobile teams will not have any problems regarding accessing the organizational data as they are available at any moment. When compared to prototype on-site traditional database servers, the disaster recovery of cloud services is relatively effective, fast, and responsive. In other words, it will not take weeks to restore data out of a disaster with cloud database systems.
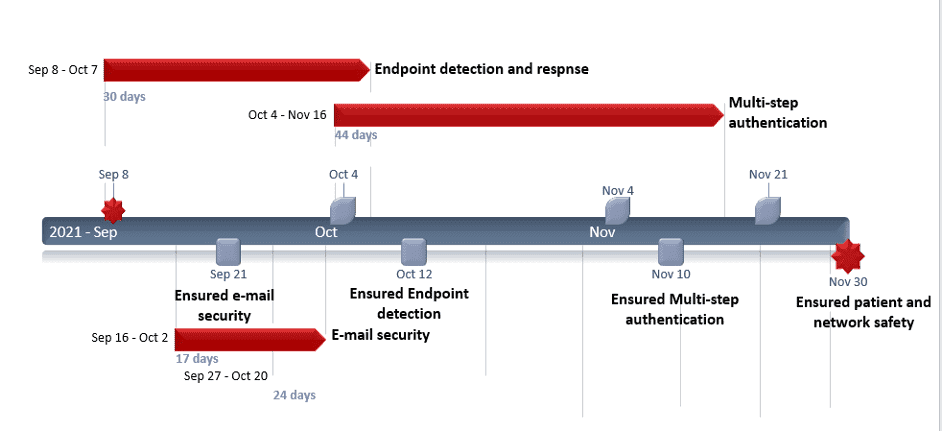
Project Timetable
According to the project timetable above, the project will start with end-point detection and response security measures. During the process, email security measures will be taken to prevent email malware and probable breaches. The project will then continue with multi-step authentication, which will approximately take 50 days. After all, patient and network security will be drastically boosted for both organization and the patient
Implementation Plan Insights
| Activity | Involved | Goals | Subtasks | Assigned to |
|---|---|---|---|---|
| Define goals | IT team | Network Security | E-mail sec. / Multi factor | NI |
| Kick-off Meeting - phase 1 | IT team | Network Security | Define problems | NI |
| Open Questions | IT team/All Team | Network Security | Define more problems | NI/All team |
| Analysis data | IT team | Network Security | Gather more insights | NI |
| Team meeting | IT team | Network Security | Discuss solutions | NI/All team |
| Plan a draft of your strategy | IT team | Network Security | Timetable | NI |
| Team meeting 2 | IT team | Network Security | Discussion | NI |
| Re-planning | IT team | Network Security | NI | |
| Deadline 1st goals | IT team | Network Security | Analysis and Process | NI |
| Define goals phase 2 | IT team | Network Security | Analysis and Process | NI |
| Kick off meeting phase 2 | IT team | Network Security | Analysis and Process | NI |
| Open Questions phase 2 | IT team/All team | Network Security | Discussion and Brainstorming | NI |
| Analysis data phase 2 | IT team | Network Security | Analysis of Solution | NI |
| Team meeting phase 2 | IT team | Network Security | Process Evaluation | NI |
| Plan a draft of your strategy phase 2 | IT team | Network Security | Process Conclusion | NI |
Conclusion
Organizational and business world has drastically been changed in recent decades. In this sense, one cannot neglect the importance of digital network and data security when it comes to managing organizations and institutions, especially in today’s increasingly digitalizing world. Subsequently, data breaching and network security have become the main agendas of such institutions. In this direction, authorities have concentrated on implementing different strategies to combat against such breaches and data losses due to hacking or lack of system specification. In this assignment, a system proposal regarding the patient, network and data safety has been presented. Accordingly, email security, end-point detection and response, and multi-factor authentications have been listed as recommendations, and related timetable and schedule have been presented. After all, authorities should implement these critical measures to prevent probable threats regarding network and safety data.
References
The Effects of Computer Hacking on an Organization. (2019). Small Business - Chron.com.
Free Timeline Templates for Professionals. (2020). Office Timeline.
Hacking Prevention: Tips to reduce your attack surface. (2020, March 19). AlienVault is Now AT&T Cybersecurity.
Healthcare Under Attack. (2018). Network Security, 2018(6), 2. https://doi.org/10.1016/s1353-4858(18)30050-3
Industrial Network Security. (2016). Network Security, 2015(3), 4. https://doi.org/10.1016/s1353-4858(15)30014-3
Khanum, S., Souza, M., Naz, N., Sasso, G., Brüggemann, O., & Heideman, I. (2016). The use of networking in nursing practice —An integrative review. Societies, 6(3), 22. https://doi.org/10.3390/soc6030022
Thank you for reading. If you need further information, feel free to have a look at our essay samples or contact us at live chat.
Contents
Recently on Tamara Blog

Essay on Animal Farm by Orwell – Free Essay Samples
“Animal Farm” by George Orwell is a literary masterpiece that tells the story of a group of farm animals who rebel against their human farmer and establish a socialist community based on the principles of equality and mutual respect (Orwell, 1945). However, over time, the pigs who lead the revolution gradually become corrupted by power and begin to oppress and exploit the other animals, ultimately turning the farm into a totalitarian state.

Essay on Cyberbullying – Free Essay Samples
Bullying is an aggressive behavior that is intentional and repeated, aimed at causing harm or discomfort to a person, and often takes place in social environments such as schools, workplaces, and online platforms. Cyberbullying is a relatively new form of bullying that has emerged with the widespread use of technology and the internet. Cyberbullying refers to bullying behaviors that occur online or through electronic means, such as social media, text messages, and emails.

Essay on Nature vs. Nurture – Free Essay Samples
The debate over nature versus nurture has been a longstanding topic of interest among psychologists and other scholars. The two concepts, nature and nurture, are frequently used to explain human development and behavior.

Lord of the Flies Essay – Free Essay Samples
Veterans have played a critical role in the history of the United States, serving their country in times of war and peace. Despite their sacrifices, many veterans face significant challenges, including physical and mental health issues, homelessness, and unemployment.

Why Veterans Are Important – Free Essay Samples
Veterans have played a critical role in the history of the United States, serving their country in times of war and peace. Despite their sacrifices, many veterans face significant challenges, including physical and mental health issues, homelessness, and unemployment.

American Dream Essay – Free Essay Samples
The American Dream has been a central concept in American culture for decades, representing the idea that anyone, regardless of their background, can achieve success and prosperity through hard work and determination. The concept of the American Dream is rooted in the country’s history and has been promoted in various ways, from the founding fathers’ beliefs to the post-World War II era.